Automate Root & Local Accounts Password Rotation with Ansible & Bitwarden
Managing privileged accounts passwords poses a significant challenge for IT organizations. Healthy password hygiene is necessary to manage your personal passwords, and it is certainly a must in any organization. Regulations and security standards require regular password rotation or password expiry date. Achieving this manually is a very time consuming (and boring) task. Let’s automate it!
Introduction
First, let’s introduce the two key elements needed to perform this task automated: a secret vault and an automation engine.
Secret Vault
In our case, we use Bitwarden password manager. It has an API, a great browser integration, autofill options, and it is actively maintained. That’s a very popular solution.
Seeking for Bitwarden licenses?
Automation Engine
Here our choice is Ansible Automation Platform by Red Hat, it’s easy to use, integrated with a ton of different software and devices. It’s the right solution for this job as it can connect to your secret vault and perform the active password change on your servers or applications.

ASP is a trusted Red Hat partner.
Note that if your secret vault has an API or a CLI interface, you should be able to implement a workflow similar to the one we’ve implemented with Bitwarden Password Manager.
A representation of the high-level steps that we are going to take:
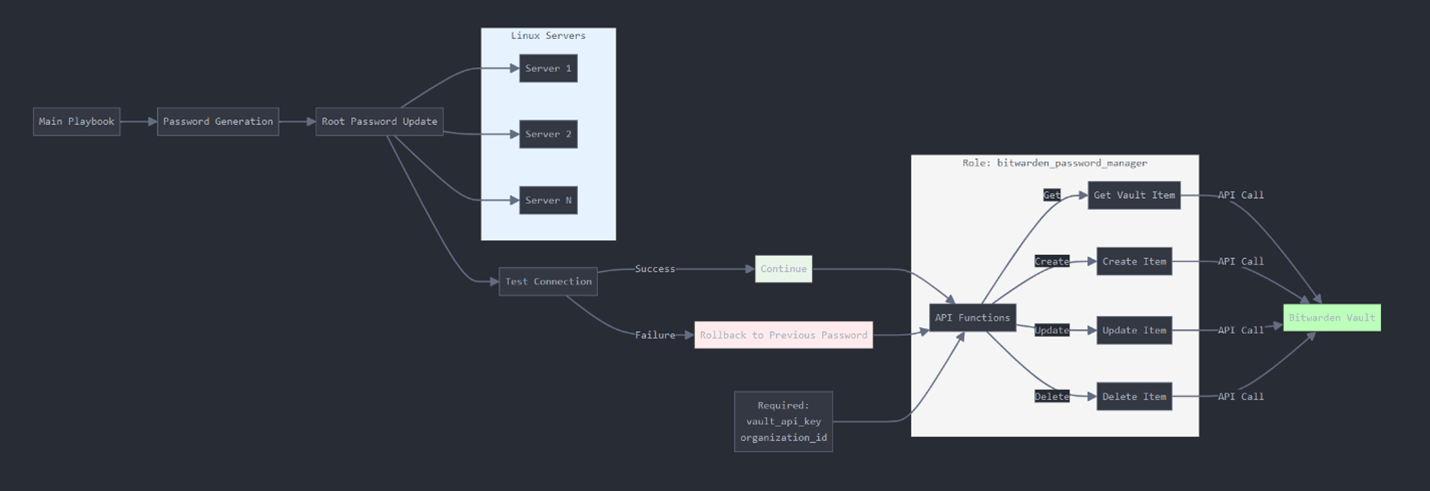
- We generate a new password that corresponds to our security requirements
- We update the target account on the target servers
- We test if the password change has been performed successfully, if not we roll back and create an incident or send a notification
- Then we search for the account entries in our password vault, and we update it
Technical details
A word of caution before starting: password rotation should be tested before being implemented in production. Make sure you have fallback authentication as you could very well be locked out of your system if one of the steps in the rotation fails.
Bitwarden API
To interact with Bitwarden vault items, note that Bitwarden provides two distinct APIs:
- “Public” API : for organization management, user administration, access control.
- Vault API (our focus) : secret manipulation, requires bitwarden CLI usage (more details here: https://bitwarden.com/help/cli/)
Once installed, Bitwarden CLI package can start a local web server acting as a proxy (only accepting localhost API calls) and interacting securely with your vault in the cloud or on-premise using an authenticated CLI session.
Once authenticated with bw login, here is the output of bw status:
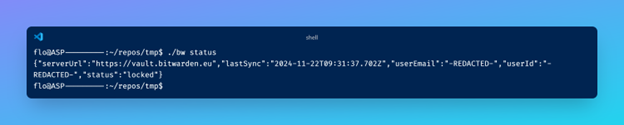
After that, start the webserver using Bitwarden serve. It will run on port 8087 by default.
To enhance security when handling such a critical API, it’s recommended to implement a controlled approach using Ansible’s execution environments (find the documentation here):
- Create a custom execution environment (container) that includes:
- Bitwarden CLI (bw)
- All required dependencies
- Secure Workflow:
- Container starts only during the password rotation timeframe
- Bitwarden API proxy server is launched within the contained environment
- Password rotation tasks are executed
- Container is stopped immediately after completion
This approach significantly reduces the attack surface by:
- Limiting API exposure time
- Isolating the API server in a containerized environment
- Ensuring the service is available only during the required operational window
The execution environment is spun-up by Ansible Automation Platform only when needed, providing a “just-in-time” access model for vault operations.
Let’s dig deeper
Bitwarden Password Manager – Create an Ansible role
After a quick analysis, we decided to create a simple role to handle API interactions.
This role is responsible for configuring the API, making it usable and interacting with it supporting the different following operations: Create, Delete, Update and Read.
NOTE : All the code has been published to github, you can find the link at the bottom of this post.
Setting up actions & scheduling
When you call the role, operation is a mandatory variable. With it, you can decide and control which action you want to perform at a given time.
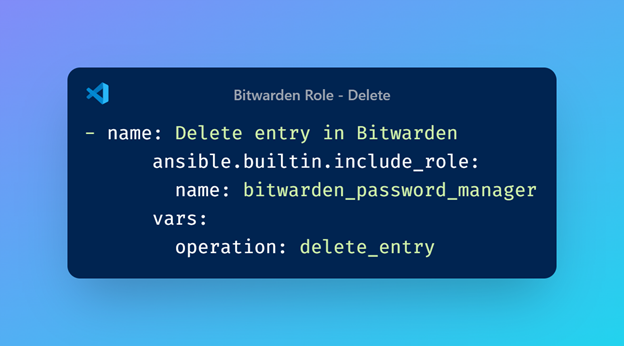
Then, it will first go through the main file and run the API call you previously defined.
All the API calls were created using the official Bitwarden documentation.
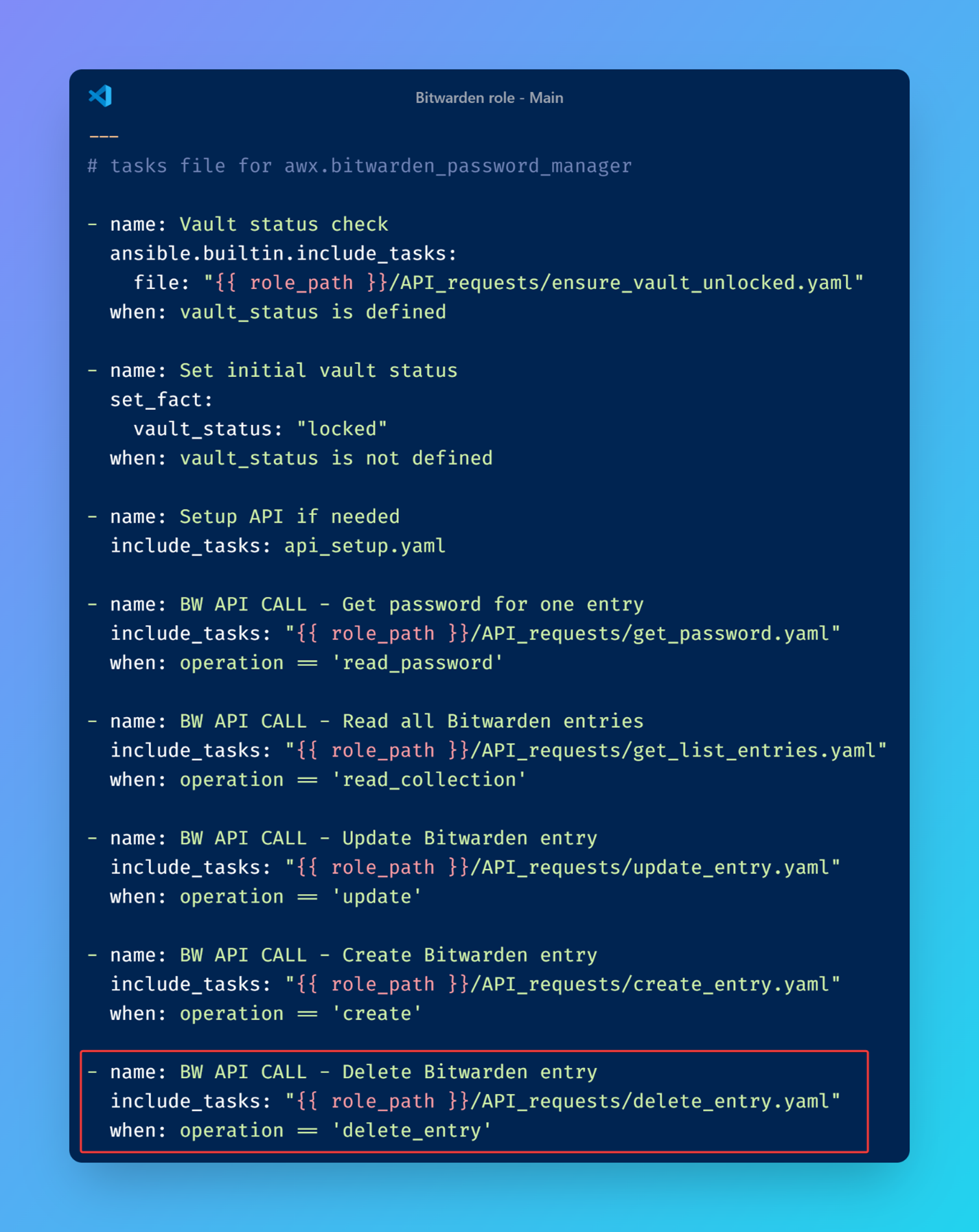
After configuring the proxy server, the role will trigger the API call we chose earlier.
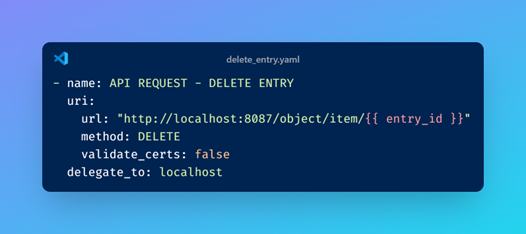
Note:
The validate_certs: false setting disables HTTPS certificate validation in the URI module. While this might raise security concerns, the implementation is carefully secured: By default, the Bitwarden API endpoint is only accessible via localhost, and the proxy server is active exclusively during Bitwarden operations. This architecture, aligned with Bitwarden’s official documentation, ensures that the HTTP-only communication remains contained within a controlled local context, effectively mitigating potential security risks.
Custom Ansible Execution Environment
As said before, to use Bitwarden’s API, “bw” CLI binary from Bitwarden is needed.
Unfortunately, the CLI is not included in Ansible’s default execution environments; therefore, a custom one must be created.
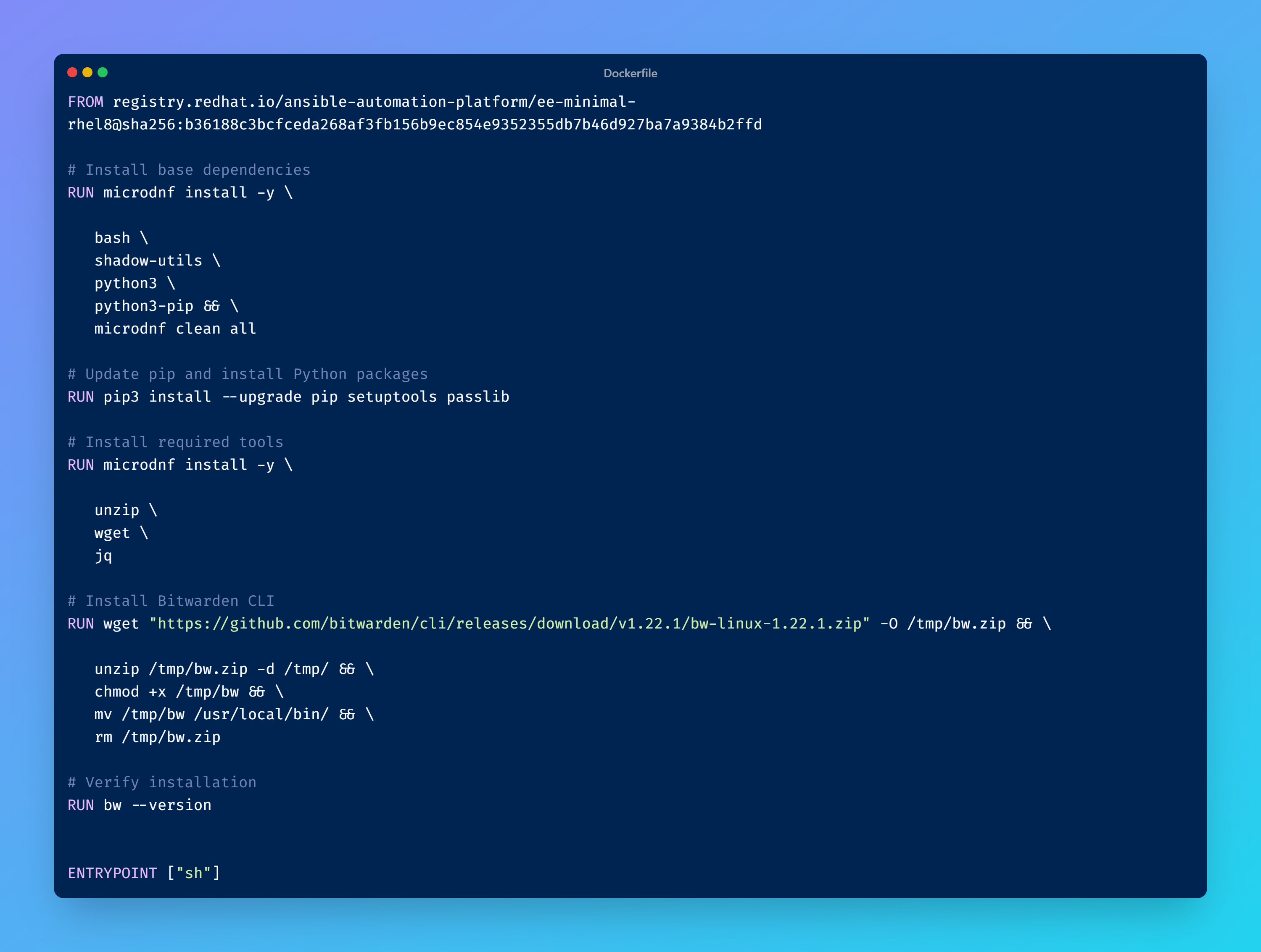
After having created a container’s image, push it to the Red Hat Private Automation Hub. It is now usable by AAP.
Password rotation
The major challenge here is to know which entry must be updated and what happens if there’s an error at the password rotation task.

For Ansible to find efficiently which Bitwarden entry has to be modified, make a custom field in which you will write the VM name (or inventory hostname in Ansible terms).
Then, Ansible will search for the matching entry and if it exists, it will proceed to the password rotation on the Linux system. If it doesn’t exist or does not find it, the whole automation stops before modifying anything.
What happens after these tasks? You already know the answer!
Call the Bitwarden Password Manager role with an “update” operation to switch the old password with the one you just created. Bitwarden will keep the old password in case something didn’t go as planned.
Note: We also use “no_log: true” to avoid getting plain-text passwords in AAP’s dashboard. We highly advertise to use this on production systems!
We run also this workflow for each new server deployment, and at server decommission using the delete operation to keep or password vault clean
Conclusion
Using Red Hat Ansible Automation Platform and Bitwarden Password Manager, you can manage to schedule a weekly password rotation targeting privileged accounts on our Linux servers.
At ASP, we are committed to open-source principles. In keeping with this philosophy, we are proud to release both our custom Ansible role for Bitwarden Password Manager and its associated execution environment.
Bitwarden Execution Environment: asp_be/bitwarden_exec_env · Quay
Bitwarden password manager role: asp-be/bitwarden_password_manager-role: Simple role to handle bitwarden password
We can help you
ASP helps businesses adopt and effectively leverage advanced solutions to optimize their IT infrastructure, enhance security, and improve overall business operations. With our deep expertise and proven track record, we manage your IT while you can focus on your business objectives.

